Deploying an Active Directory domain in a perimeter network (or DMZ) usually requires some changes in firewalls. But the question is: what ports and from what computers must be opened?
The answer is not obvious. To simplify the firewalls rules deployment and (very important!) to simplify communication with Network Support team I designed an Excel spreadsheet. The spreadsheet has only one page that includes all groups and rules that must be configured on a firewall. You can easily customize it and then share with the network administrators.
The default rules included in the spreadsheet assumes:
- One-way trust from the domain in the DMZ to an internal domain
- The domain in DMZ contains domain controllers as well as member servers
- Typical clients must be installed within the DMZ domain on all servers. The clients must communicate with relevant server components in the internal network
The network topology diagram is below:
You can download the files here. The folder includes:
- Visio diagram;
- Excel spreadsheet;
- Zip archive with the two files above.
How to use the spreadsheet
Step 1. Update server groups
Network administrator will use these lists to create firewall groups.
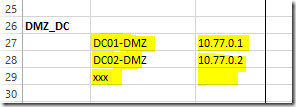
List all domain controllers of the internal domain here:
List all domain controllers of the DMZ domain here:
List all servers (including DC and member servers) of the DMZ domain here:
Step 2. Review the rules and adjust as needed
Update the main table that includes actual rules. The table is pre-populated with some known rules.
The table contains three main groups, that combine rules required for specific functions.
The DMZ specific domain controllers rules group includes communication for DNS and Time Synchronization. Typically, DNS service runs on domain controllers; time synchronization with external time source is required on domain controllers as well.
The Infrastructure rules group includes communications that must be enabled from ANY server in the DMZ network to specific servers in the Internal network. Typically they are SCCM, SCOM, Antivirus, Backup. Two very important rules are also Remote Desktop access and Windows Activation. Note: update the rules marked with ??? if you have these infrastructure components deployed.
The Active Directory one-way forest trust group includes ports that must be opened specifically for Active Directory trust. Note: trust relationships include communication that can be initiated from ANY server in the DMZ network (i.e. either domain controller or member server) to domain controllers in the Internal network.
Quick description of the table columns:
| Column | Description |
| Service | Service/application name that requires the rule |
| DMZ - Group | Group of servers in DMZ network that initiates or accepts connection. Add either a predefined group or individual servers or IP addresses here. |
| DMZ - Port | Port or ports used to initiate or accept the connection |
| Direction | ---> DMZ initiates connection to Internal <--- Internal initiates connection to DMZ <-> both directions (don’t use) |
| Internal - Group | Group of servers in Internal network that initiates or accepts connection. Add either a predefined group or individual servers or IP addresses here. |
| Internal - Port | Port or ports used to initiate or accept the connection |
| Explanation | Your own reminder, why you need this rule |
You can easily filter the rules (see row 5 with drop-down lists).
And one more link to the files. The folder includes:
- Visio diagram;
- Excel spreadsheet;
- Zip archive with the two files above.
Feel free to customize the files the way you want.







Хорошая статья, спасибо!
ReplyDeleteJust what I was looking for.
ReplyDeleteThank You
https://bayanlarsitesi.com/
ReplyDeleteManisa
Denizli
Malatya
Çankırı
0FZD62
Antalya
ReplyDeleteAntep
Burdur
Sakarya
istanbul
284
Batman
ReplyDeleteArdahan
Adıyaman
Antalya
Giresun
YD5R60
whatsapp görüntülü show
ReplyDeleteücretli.show
GR4V
Antep Lojistik
ReplyDeleteYalova Lojistik
Erzincan Lojistik
Tekirdağ Lojistik
Elazığ Lojistik
0OMRSA
D453D
ReplyDeleteAdana Evden Eve Nakliyat
Afyon Lojistik
İzmir Parça Eşya Taşıma
Elazığ Lojistik
Konya Parça Eşya Taşıma
8FE85
ReplyDeleteSilivri Çatı Ustası
Uşak Evden Eve Nakliyat
Silivri Cam Balkon
Kırşehir Evden Eve Nakliyat
Binance Güvenilir mi
A598E
ReplyDelete%20 indirim kodu
13CA7
ReplyDeletebayburt canlı sohbet ücretsiz
Gümüşhane Mobil Sohbet Sitesi
Karabük Mobil Sesli Sohbet
kadınlarla ücretsiz sohbet
canlı sohbet bedava
bursa canlı görüntülü sohbet siteleri
samsun ücretsiz sohbet
Adana Bedava Görüntülü Sohbet
sakarya mobil sohbet
F1489
ReplyDeletebingöl görüntülü sohbet odaları
artvin sesli sohbet
sesli sohbet sitesi
ücretsiz sohbet uygulaması
Niğde Görüntülü Sohbet
erzurum mobil sohbet
bedava sohbet uygulamaları
sesli mobil sohbet
gümüşhane canlı sohbet ücretsiz
FF693
ReplyDeleteBinance Borsası Güvenilir mi
Mith Coin Hangi Borsada
Telegram Görüntüleme Satın Al
Xcn Coin Hangi Borsada
Binance Referans Kodu
Coin Madenciliği Nasıl Yapılır
Ort Coin Hangi Borsada
Shinja Coin Hangi Borsada
Coin Kazma Siteleri
E5EED
ReplyDeletethorchain
uniswap
sushiswap
dappradar
zkswap
quickswap
yearn finance
DefiLlama
pancakeswap
شركة صيانة افران mMqqcn9eor
ReplyDeleteشركة مكافحة حشرات بالجبيل 7vfTRzj9Ho
ReplyDelete64CFF751C8
ReplyDeleteinstagram takipçi alma ucuz